Why do you need information security?
Why do you need information security?
In addition to protecting your assets, VDA audits or ISMS 27001 certifications are becoming increasingly strong selection criteria for e.B. OEMs. New data protection regulations also make information security concepts indispensable. Suppliers who invest here enjoy a clear advantage over their competitors.
How does information security become a competitive advantage?
Companies with solid information security practices present themselves more robustly and can not only survive an emergency situation, but emerge stronger from it.
Information security is primarily based on good risk management:
In this way, companies not only identify possible threats and risk factors, but also opportunities that arise, such as new business areas.B, such as new business areas.
What can we do for you?
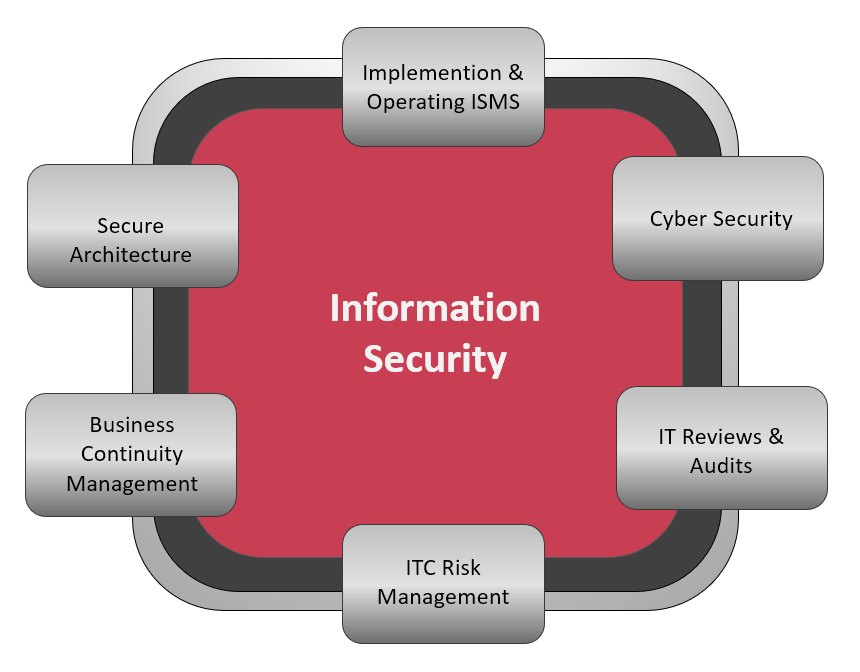
RMTP offers in this context:
- Establishment, introduction and operation of an ISMS
- Advice on data protection relevant topics in accordance with the new General Data Protection Regulation (GDPR) as part of information security
- Cybersecurity Reviews and Audits
- Risk and emergency management
- Information Security Architecture (ISA)
Our services in detail
Implementation and operation of an ISMS
- Assessment, planning and definition of strategies and objectives for information security
- Planning and implementation of an ISMS
- Creation of safety guidelines and guidelines according to national and international standards (e.B.ISO 27000 series)
- Introduction / development of information security organizations and key performance indicators (KPI)
- Security process design, management, optimization and implementation, including supporting processes (oriented to ITIL and COBIT)
- Interim Manager Information Security (e.B.g.: CISO, ICT Security Manager, Security Officer)
- Design of control measures, requirements and activities
- Data protection-relevant topics in accordance with the new General Data Protection Regulation as part of an ISMS, development and integration into existing structures
Cyber Security
- Planning and implementation of cyber security frameworks (e.B. NIST Cybersecurity Framework)
- Implementation and evaluation of hazard identification methods, requirements, procedures and activities according to ISO 27002
- Review and customer-specific adaptation of techniques for detecting system vulnerabilities
- Planning and management of information and communication technology and information security processes to prevent and contain harmful content (e.B. antivirus solutions)
- Cyber Security Process Design, Management, Optimization and Implementation (according to ITIL and COBIT)
IT reviews and audits
- Review of security concepts and measures
- Preparation and support of ISO 27001 certifications and safety analyses
- Creation and management of audit programs for information and telecommunications technology (ICT) and information security
- Execution of system, process and service audits
- Audits, analyses and advice on compliance and due diligence requirements
- Concept development and implementation of self- and security assessments
ICT Risk Management
- Conception, creation and implementation of risk management systems according to common standards (ISO/IEC 27005, M_o_R, Risk_IT)
- Creation of asset management concepts and implementation of solutions for the identification of assets
- Implementation of threat analyses, protection needs assessments, business impact analyses, risk analyses and assessments
- Preparation of risk assessments and treatment plans
- Process integration into Enterprise Risk Management (ERM) systems and vulnerability management
- Moderation, process training, tool support for ICT risk management
Emergency Management/BCM
- Consulting, conception and planning of emergency management (BCM, z.B.ISO 22301), emergency preparedness systems (DRP, e.B.ISO 24762) as well as local and global data backup strategies
- Consulting and preparation of precautionary concepts and emergency manuals for data centers, technical and telecommunications rooms
- Creation of concepts and support of Security Operation Centers, CERT/CSIRT
- Advice on emergency management, crisis management and communication management
- Creation and support of test and exercise plans, including scenario development
IS Architecture
- Conception and implementation of an information security portfolio and IT service catalogue
- Design and design of organizational computer and network security infrastructure according to corporate policies, customer requirements, external regulations, and business risks
- Review and development of security concepts, contract drafting for technical services and sourcing concepts
- Analysis, identification of weak points and gaps in existing and agreed security architecture concepts, as well as recommendations for changes or improvements
- Consulting and solution recommendations for security solutions, at the interface between business requirements and information security requirements
- Management of access rights, identity management, logical and physical protection
We are happy to work with you to develop your information security solutions.
Contact us directly!
Your contact persons:
Ralf Mekelberger
Mail: informationssicherheit@rmtp.de
Telephone: +49 30 6098 1892 0